Basic Information of HEUR:Exploit.java.CVE-2013-2423.gen
Name: HEUR:Exploit.java.CVE-2013-2423.gen
Type: Trojan Horse
Vulnerable browser:IE explorer, Google Chrome, Mozilla Firefox etc.
Targeted OS: win xp, win7, win vista, win8
Route of transmission:spam email, infected website, software package, shared file and so on.
Learn More about HEUR:Exploit.java.CVE-2013-2423.gen
HEUR:Exploit.java.CVE-2013-2423.gen is classified into the devious Trojan horse group This fake program is designed to invade vulnerable websites and make up fake items which used to trick or threaten computer users. When you accidentally visit malicious websites or open spam email or other files containing the activation code of this virus, it can sneak into your computer very easily.
Once enter your computer, this unwanted program starts making up fake items which you have never seen before and displaying them to you. You are not familiar with these items you are not sure about whether there is really threat on your computer. So you are likely to be tricked by its lie and then to download its software or pay money for its product which actually is totally useless or even devious.
What’s more, it is busy tracking and recording your internet activity data while convincing you and promoting commercial. Via using keyloggers and collecting your information, it may lead its designers to access your computer remotely and compromise your privacy and security.
Malicious Actions that HEUR:Exploit.java.CVE-2013-2423.gen May Perform
2. HEUR:Exploit.java.CVE-2013-2423.gen modifies your system settings and hides deeply behind your system;
3. HEUR:Exploit.java.CVE-2013-2423.gen may hijack your browser and prevent you to accessing wanted information;
4. HEUR:Exploit.java.CVE-2013-2423.gen displays fake messages and alerts to trick you into paying for its useless product and downloading more threatening malware.
5. HEUR:Exploit.java.CVE-2013-2423.gen opens doors for cyber hackers to access your computer by collecting and stealing your personal information.
Guides to Remove HEUR:Exploit.java.CVE-2013-2423.gen
Manual removal guide:
Keep pressing F8 until Windows Advanced Options meanu shows up, then use arrow key to select Safe Mode with Networking and press Enter.

Step 2: Use windows Task Manager to end HEUR:Exploit.java.CVE-2013-2423.gen processes.
(Press CTRL+ALT+DLE or CTRL+SHIFT+ESC to launch Task Manager.)

Step 3: Remove these associated files on you’re the local disk such as:
%Documents and Settings%\All Users\ Application Data\HEUR:Exploit.java.CVE-2013-2423.gen
%AllUsersProfile%\Application Data\ HEUR:Exploit.java.CVE-2013-2423.gen. dll
%AllUsersProfile%\Application Data\ HEUR:Exploit.java.CVE-2013-2423.gen exe
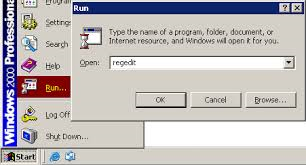
Step 4: Go to the Register Editor and delete the following entries:
(Hit Win+R keys and then type regedit in Run box to search. )
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run HEUR:Exploit.java.CVE-2013-2423.gen HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run HEUR:Exploit.java.CVE-2013-2423.gen. exe”
Note:as the steps in this removal guide refer to key parts of the system, expert skills are needed to finish the removal process. If you are unfamiliar with the steps and you don’t want to take the risk of damaging the system,
you are advised to download the most popular malware remover SpyHunter to automatically scan your PC and delete the unwanted program.
Automatic removal guide:
1) Click the icon below to download SpyHunter automatically

2) Follow the instructions to install SpyHunter



3) Run SpyHunter to detect HEUR:Exploit.java.CVE-2013-2423.gen
Run SpyHunter and click "Malware Scan" button to scan your computer, remove all detected items after scanning.

Hope the manual tips could walk you through how to erase HEUR:Exploit.java.CVE-2013-2423.gen infection. If the manual removal process is too abstract for you to execute , please feel free to start an automatic removal with the best HEUR:Exploit.java.CVE-2013-2423.gen remover right now.

